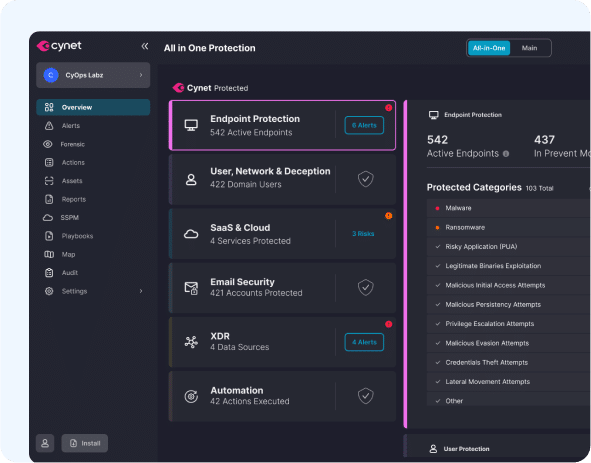
Top MITRE ATT&CK Performance
Cynet amazed the cybersecurity market by outperforming virtually all endpoint protection vendor platforms in the 2023 MITRE Engenuity ATT&CK Evaluation: Enterprise. For the first time in MITRE history, Cynet detected 100% of all threats tested (143 of 143) and provided 100% analytic insights for all detected threats (all 143 threats), without the need for configuration changes! Not a single vendor performed better than Cynet.