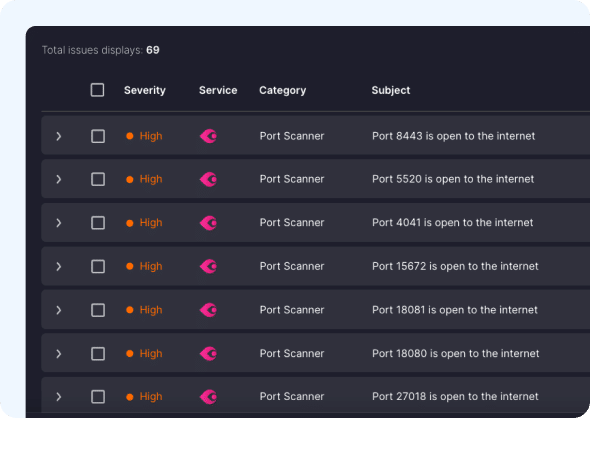
Automatically Discover SaaS Risks
Gain comprehensive SaaS security risk detection and remediation capabilities to your Cynet dashboard. Continuously monitor configuration settings across your SaaS applications and hunt for security posture issues without the need to access additional panes of glass.