Let’s get started!
Ready to extend visibility, threat detection and response?
Get a DemoEDR, which stands for Endpoint Detection and Response, is a cybersecurity technology that continuously monitors devices to detect and respond to cyber threats like ransomware and malware. Endpoint detection and response (EDR) is a cybersecurity system that monitors endpoints for security threats. The goal of EDR is to detect breaches as they happen and respond quickly to threats. It gathers and analyzes information related to security threats on computer workstations and other endpoints, making it possible to identify security breaches as they happen and facilitate a quick response.
EDR is also known as endpoint detection and threat response (EDTR). It’s designed to protect an organization’s users, devices, and IT assets from cyber threats that get past antivirus software and other security tools. EDR can detect threats like ransomware and malware. It combines real-time monitoring and data collection with automated analysis and response, and can flag files that show signs of malicious behavior.
EDR works by:
The global EDR market was valued at $2.87 billion in 2022. It’s projected to grow to $10.79 billion by 2028.
This is part of an extensive series of guides about data security.
Cyber threats are constantly evolving, with attackers using increasingly sophisticated tactics to bypass traditional security measures. EDR helps organizations stay ahead of these threats by providing continuous monitoring, detection, and response capabilities.
The rise of remote work has expanded the attack surface, as employees connect to corporate networks from various locations and devices. EDR helps secure these dispersed endpoints by providing centralized monitoring and management, ensuring consistent security across all devices.
EDR accelerates incident response by automating threat containment and remediation actions, reducing the time it takes to address security incidents. This minimizes potential damage and business disruption caused by cyberattacks.
EDR reduces the amount of time attackers can remain undetected within a network (dwell time) by promptly identifying and addressing security incidents. Minimizing dwell time is crucial in limiting the potential damage caused by a cyberattack.
EDR helps organizations shift from a reactive security approach to a more proactive one, where potential threats are detected and mitigated before they can cause significant harm. This proactive approach can significantly reduce the risk of data breaches and other security incidents.
EDR tools are technology platforms that can alert security teams of malicious activity, and enable fast investigation and containment of attacks on endpoints. An endpoint can be an employee workstation or laptop, a server, a cloud system, a mobile or IoT device.
EDR solutions typically aggregate data on endpoints including process execution, endpoint communication, and user logins; analyze data to discover anomalies and malicious activity; and record data about malicious activity, enabling security teams to investigate and respond to incidents. In addition, they enable automated and manual actions to contain threats on the endpoint, such as isolating it from the network or wiping and reimaging the device.
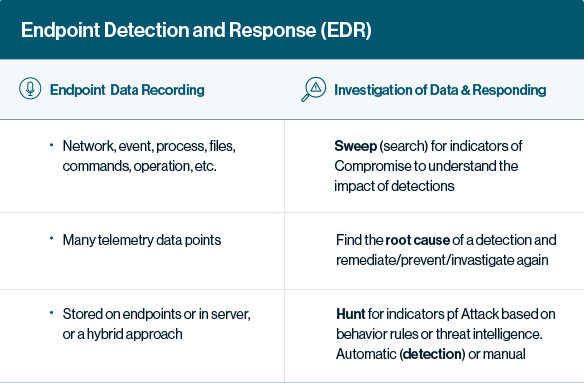
EDR solutions continuously ingest data from endpoints, including event logs, running applications, and authentication attempts. Here is how the process usually works.
Gathering Data
The first step involves:
Analyzing Data
Next, the EDR solution needs to use the data to provide actionable information:
Responding
Finally, the EDR solution acts on the analyzed data:
EDR solutions can provide automated responses to threats on endpoints. This is especially important for threats that proliferate quickly and cause significant damage before human intervention is possible.
Automated response capabilities can include actions such as quarantining infected files, blocking malicious network connections, or even completely isolating an affected endpoint from the network. This allows security teams to focus on investigating and resolving the issue without having to worry about containment.
EDR tools help security teams perform rapid analysis and forensics on detected threats. They provide valuable insights into the nature of the threat, including its origin, how it operates, and how it can be mitigated.
EDR tools can record activity on an endpoint over time, providing a historical log of events that can be invaluable during a forensic investigation. This can help security teams identify the root cause of a security incident, understand the full extent of the breach across multiple endpoints, and develop effective strategies to prevent future occurrences.
EDR solutions integrate with threat intelligence feeds, which provide detailed information about emerging threats and known malicious actors. By integrating this data, EDR tools are better able to detect and respond to new and sophisticated threats.
EDR tools can compare observed endpoint behavior to known threat indicators, improving their ability to accurately identify malicious activity. This also allows them to provide alerts about potential threats that are specific to an organization’s industry or geographical location.
Threat hunting is an advanced capability provided by some EDR solutions. This proactive approach to defense involves actively searching for signs of compromise or suspicious activity within an organization’s network that may not have been detected by automated mechanisms.
Threat hunting can identify stealthy and persistent threats such as Advanced Persistent Threats (APTs) and insider threats that can evade traditional security measures. In addition, security vendors can provide managed threat hunting services carried out by their experienced security experts.
EDR solutions provide both real-time and historical visibility into endpoint activity. Real-time visibility enables security teams to react quickly to potential threats, minimizing the window of opportunity for attackers. On the other hand, historical visibility can support forensic investigations and help identify patterns or trends that may indicate a larger security issue.
EDR tools provide a range of response options to detected threats. In addition to automated actions such as quarantining infected files or blocking malicious network connections, EDR solutions can also allow security teams to manually intervene when necessary.
These response options allow organizations to choose the most appropriate action based on the specific nature of each threat and their unique security requirements.
Below is a quick review of our top 6 endpoint protection tools that include an EDR component: FireEye, Symantec, RSA, CrowdStrike, Cybereason, and our own Cynet Security Platform. For each vendor we explain the context of the EDR module within the broader security solution, and list EDR features as described by the vendors.

The Cynet Platform is an integrated security solution that goes beyond endpoint protection, offering NGAV, EDR, UEBA, deception, network monitoring and protection.
On prem, Cloud or hybrid
Symantec’s endpoint solution includes legacy antivirus, NGAV with emulator for detecting hidden packages, memory exploit prevention, deception technology, device network firewall and intrusion prevention, and EDR.
Virtual or physical appliance
https://www.symantec.com/products/endpoint-protection
RSA NetWitness Endpoint is a solution focused on EDR capabilities. Malware protection, network monitoring, log analysis and other capabilities are offered as part of the broader NetWitness Platform.
Physical or virtual appliance
https://www.rsa.com/en-us/products/threat-detection-response/endpoint-security-endpoint-detection-response
Falcon Insight is an EDR module as part of the Falcon Endpoint Protection Enterprise solution, which also includes NGAV, threat intelligence, USB device protection, and threat hunting.
Cloud
https://www.crowdstrike.com/endpoint-security-products/falcon-endpoint-protection-enterprise/
A module within the Cybereason Defense Platform, which also includes NGAV and Managed Detection and Response (MDR).
Endpoint solution including an agent with four detection engines, NGAV capabilities, and EDR.
Appliance or cloud
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of data security.
Authored by Cynet
Authored by Cloudian
Authored by HackerOne
Endpoint Detection and Response (EDR) is a security category defined by Gartner in 2013. It is intended to fill security gaps on endpoint devices like employee workstations, servers, and mobile devices. EDR helps security teams investigate and immediately respond to malicious activities at remote endpoints to contain and mitigate attacks.
Compared with traditional endpoint security solutions, EDR provides real time information about malicious activity on endpoint devices, automatically responds to some attack scenarios, and shortens response time by security teams. EDR is an essential tool for responding to advanced persistent threats, and any attack that manages to bypass preventative defenses on an endpoint device.
EDR systems deploy agents on end-user devices, which are used to continuously monitor activity and network traffic to and from the device. These events are recorded in a central database. EDR tools analyze the data to identify incidents, investigate them, and use the data to find similar threats on other endpoints across the organization.
Most importantly, EDR allows security teams to immediately see what is happening on the endpoint and take action to contain and eradicate threats.
Antivirus software can stop threats based on malware, but is not effective against other types of threats. It also cannot protect against malware that evades detection. EDR is able to detect and respond to threats that evade antivirus and other traditional defenses on the endpoint device.
EDR solutions, on their own, do not replace antivirus. EDR is typically part of an endpoint protection platform (EPP), which includes advanced antivirus and anti-malware protection. EDR works together with antivirus – it relies on antivirus to stop some threats, but is able to detect and respond to threats that were not captured by antivirus software.
Search results for:
Request a Quote
Fill out the form below, and we’ll provide you with a quote tailored to your requirements.
Get your practical guide to the
2023 MITRE ATT&CK Evaluation
Become our partner!
Grow your business with Cynet
See Cynet All-in-One in Action
Let’s get started
Ready to extend visibility, threat detection, and response?
See Cynet All-in-One in Action