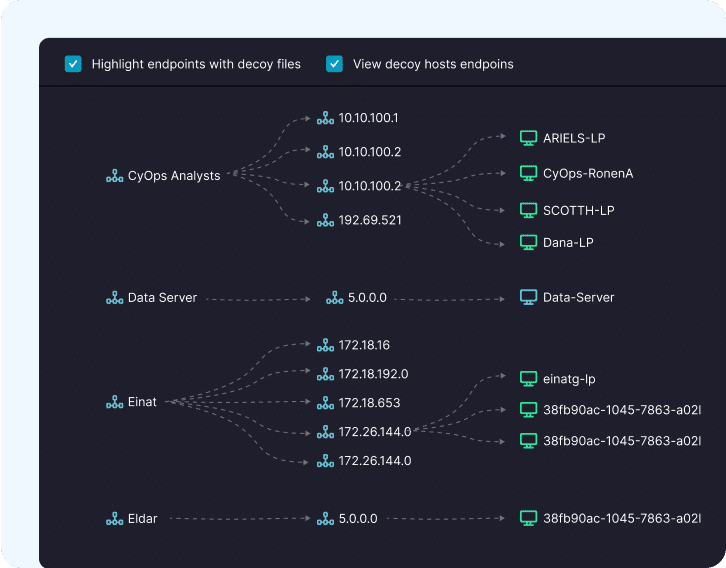
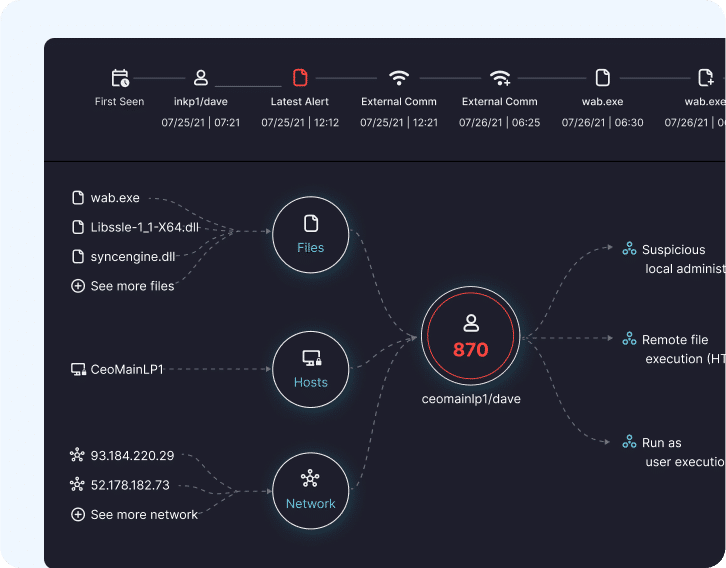
Network Protection
Cynet detects stealthy threats and anomalous behaviors across your network, analyzing interactions with devices and users to provide high fidelity threat detection. Network signals are combined with other Cynet native telemetry for unparalleled threat visibility and detection accuracy.