Let’s get started!
Ready to extend visibility, threat detection and response?
Get a DemoWritten by: Ben Gold
Attackers first began using the Ragnar Locker ransomware towards the end of December 2019 as a way to attack compromised networks. Ragnar Locker is a ransomware that runs on Microsoft Windows. It specifically targets software commonly used by managed service providers to prevent their attack from being detected and stopped. It is aimed at English-speaking users.
When the attackers first compromise a network, they will perform reconnaissance and pre-deployment tasks before executing the ransomware.
Cynet 360 protects your environment against this type of attack. This type of attack is detected by Cynet alerting you to the malicious activities, using the following mechanisms.
Note that some of the actions are set to alert only, to not interrupt the ransomware’s flow, allowing Cynet to detect every step of Ragnar Locker Ransomware attack flow.
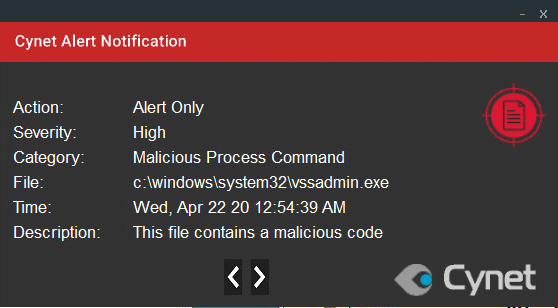
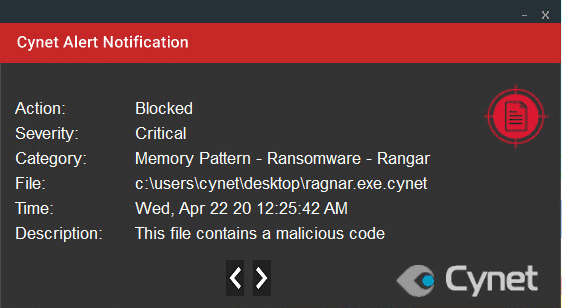
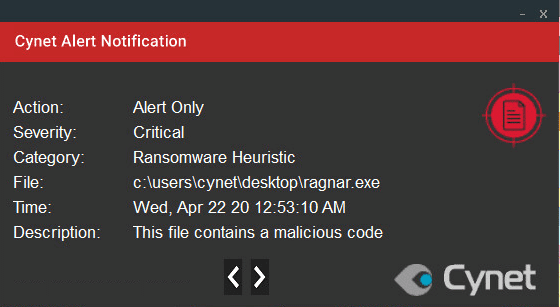
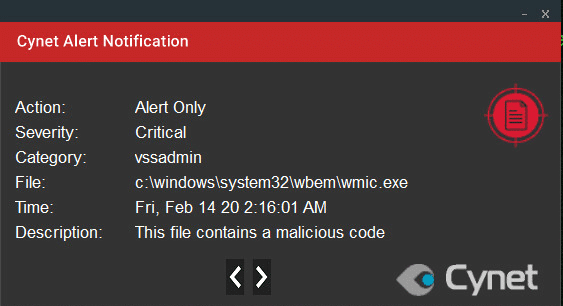
After execution, Ragnar Locker Ransomware encrypts the files and adds the extension “.ragnar” and an 8 digit number:
When encrypting files, it will skip files in the following folders, file names, and extensions:
| kernel32.dll
Windows Windows.old Tor browser Internet Explorer Opera Opera Software Mozilla Mozilla Firefox $Recycle.Bin |
ProgramData
All Users autorun.inf boot.ini bootfont.bin bootsect.bak bootmgr bootmgr.efi bootmgfw.efi desktop.ini iconcache.db |
ntldr
ntuser.dat ntuser.dat.log ntuser.ini thumbs.db .sys .dll .lnk .msi .drv .exe |
Once a computer’s files have been encrypted and renamed, it creates a ransom note at several directories – the ransom notes are named RGNR_25A5382C.txt.
The note itself contains an email address to contact the cybercriminals who will provide a decryption tool once the victim sends them the Base64 code which also contains details of the infected host.
The Cynet CyOps team is available to clients 24/7 for assistance with any issues, questions, or comments related to Cynet 360. For additional information, you may contact us directly at:
Phone (US): +1-347-474-0048
Phone (EU): +44-203-290-9051
Phone (IL): +972-72-336-9736
CyOps Email: [email protected]
Search results for:
Request a Quote
Fill out the form below, and we’ll provide you with a quote tailored to your requirements.
Get your practical guide to the
2023 MITRE ATT&CK Evaluation
Become our partner!
Grow your business with Cynet
See Cynet All-in-One in Action
Let’s get started
Ready to extend visibility, threat detection, and response?
See Cynet All-in-One in Action