Zero-Trust Detections: How Cynet Protects Customers from the New OneNote Campaign

In the last couple weeks, we have observed a new threat actor attack method to abuse the Microsoft OneNote application by weaponizing documents with embedded malicious code. Qakbot threat actors are massively distributing a malicious spam email with “.ONE” (OneNote document) files. We have also observed that IcedID and Bumblebee threat actor have also switched to malicious OneNote lures.
Cynet provides comprehensive visibility and protection across all attack vectors, with fully automated response workflows throughout the entire environment, all backed by a 24/7 MDR service.
Cynet’s endpoint protection platform (EPP) detects and prevents different threats, covering different tactics, techniques, and procedures (TTPs).
Cynet’s Orion Threat Research Team combats threat actors with two layers of detections, enabling Cynet EPP to protect our customers from the most well-known threats and Zero-Day attacks. The first is Cyber Threat Intelligence (CTI), which detects and prevents different threat actors and TTPs. The second is Zero-Trust logic.
The Zero-Trust logic is based on deep research of the OS operation and different trusted applications. By practicing “Know Good, Detect Evil”, we can detect the newest attacks in the wild.
The main difference between CTI logic and Zero-Trust logic is that CTI forbids certain activities, whereas Zero-Trust allows legitimate activities. Accordingly, any other activities will be unauthorized.
Threat actor groups rapidly change their TTPs to avoid and bypass security vendors. In the last year, we have noticed such adaptations in reaction to updates by Microsoft, for example, after the company announced, “We’re changing the default behavior of Office applications to block macros in files from the internet”. According to BleepingComputer, “A free unofficial patch has been released through the patch platform to address an actively exploiting zero-day flaw in the Windows Mark of the Web (MotW) security mechanism.”
Top initial attack methods used by threat actors:
- Weaponized Office Documents (Word, Excel, PowerPoint) with VBA or XLM macro version 4.0
- HTML Smuggling files luring (Obfuscated Files or Information: HTML Smuggling T1027.006)
- ISO, IMG, and VHD file images (Subvert Trust Controls: Mark-of-the-Web Bypass T1553.005)
Top malware deployed by threat actors:
- Emotet
- Qakbot
- IcedID (A.K.A BokBot)
- Details: “Shelob Moonlight – Spinning a Larger Web“
- Bumblebee
- Details: “Orion Threat Alert: Flight of the BumbleBee“
- Ursnif (A.K.A Gozi)
These malware lead to ransomware infection in most cases. However, by preventing the initial stages of the infection, Cynet protects its customers from ransomware encryption.
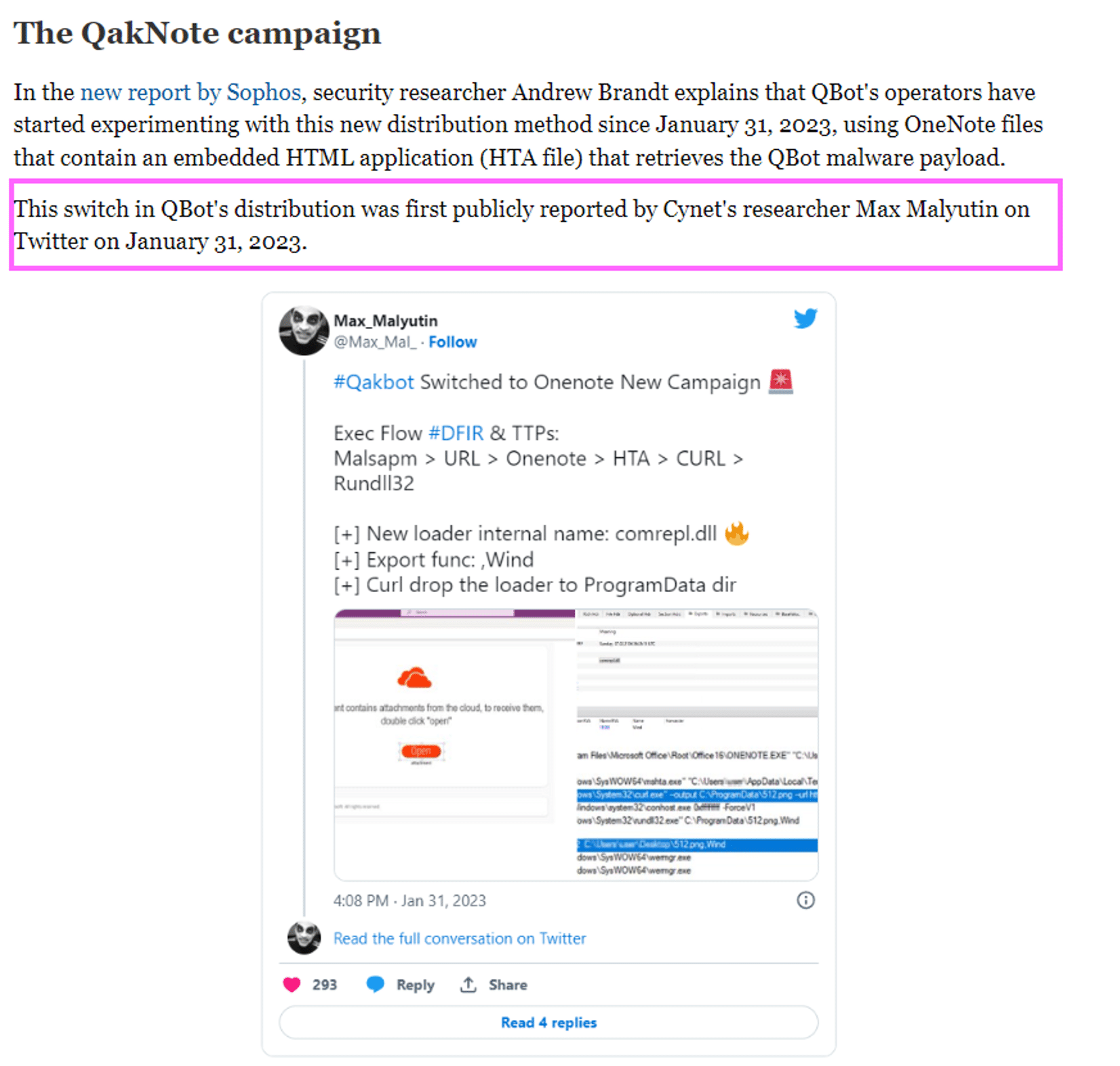
The OneNote campaign
Cynet detected and prevented this campaign (which was covered in BleepingComputer) by using the Zero-Trust logic.
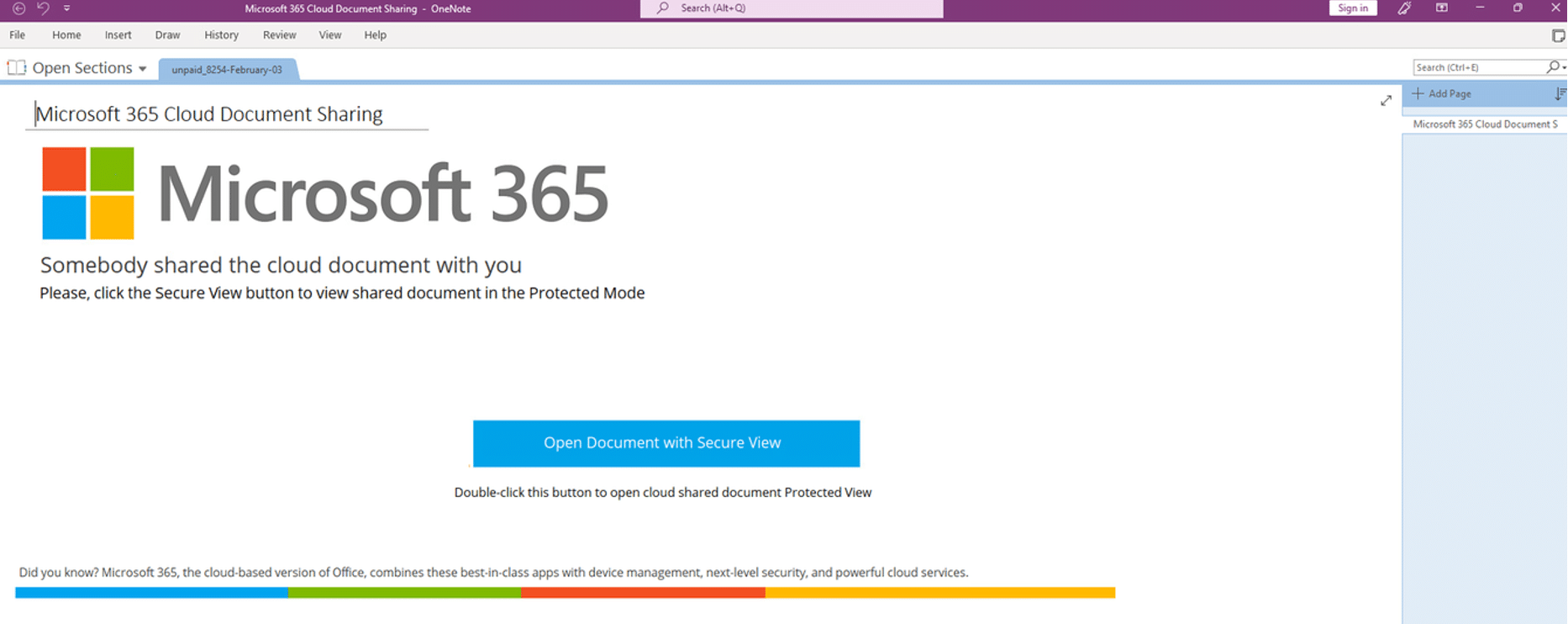
Threat actors use social engineering to lure potential victims to interact with OneNote documents. The malicious “.one” files appear to be legitimate documents.
IcedID OneNote Doc with fake Microsoft 365 template:
Qakbot OneNote Doc with fake OneNote template:
Qakbot execution flow:
IcedID execution flow:
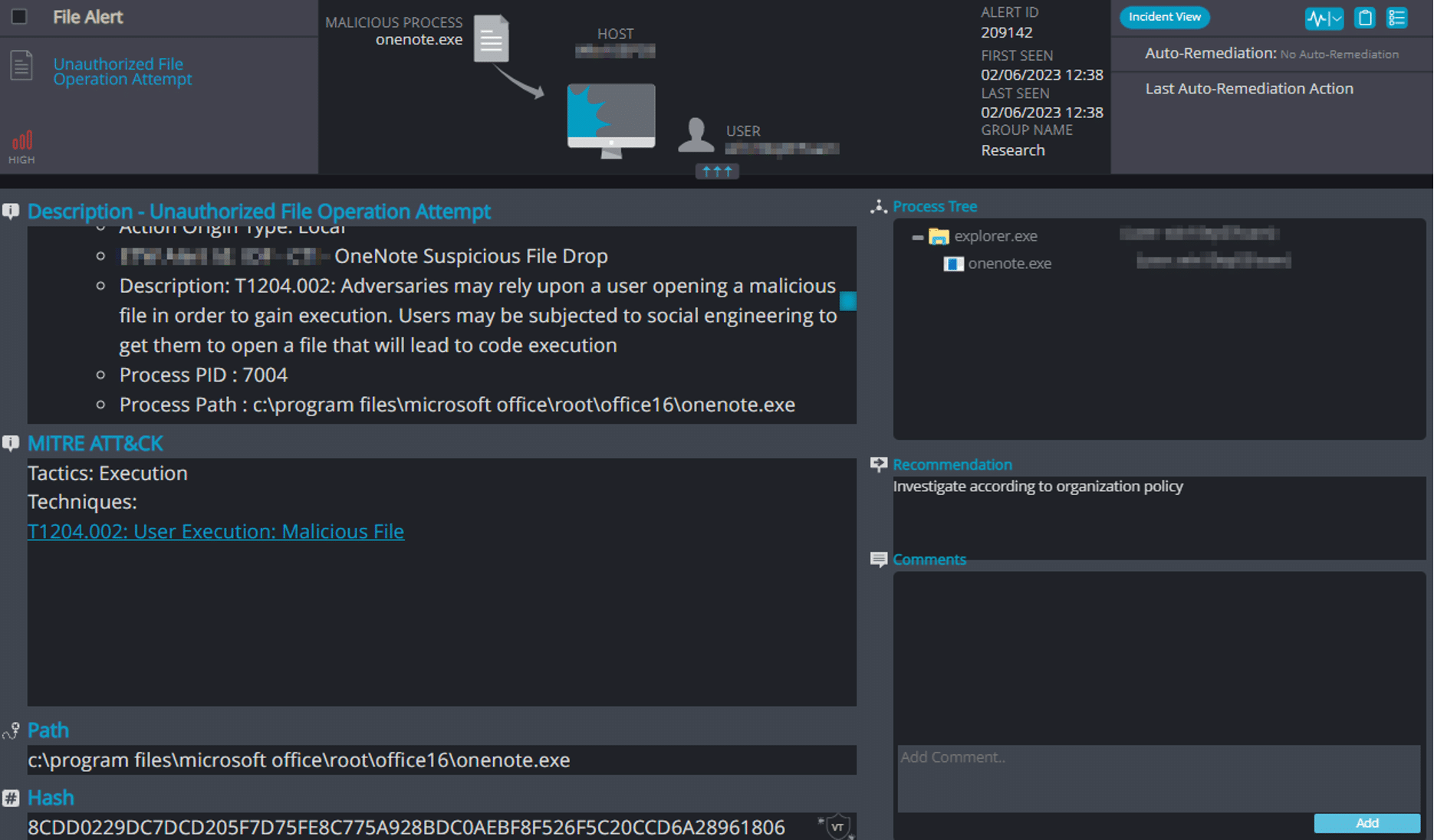
Cynet Zero-Trust logic (for OneNote) detects and prevents any abnormal execution.
Cynet Process Monitoring alert:
Cynet unauthorized file operation attempt (UFOA) alert:
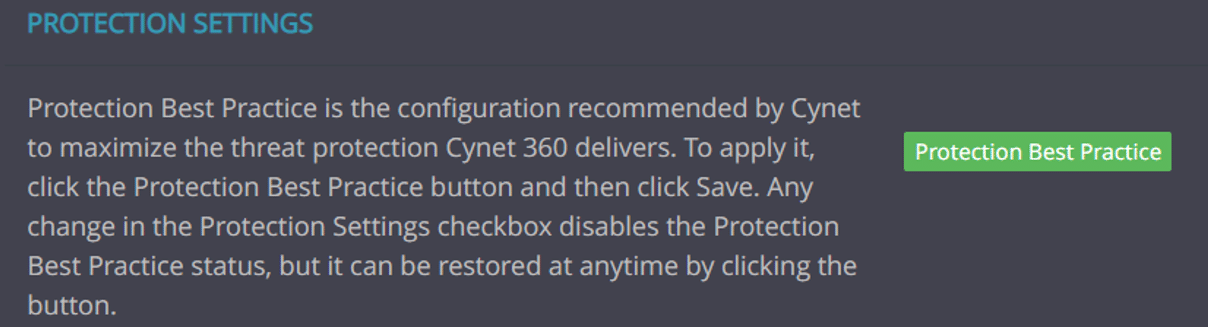
All Cynet customers running “Best Practice” settings are fully protected from this threat. With just one click, Cynet autopilot protects your organization:
We strongly suggest that all organizations take precautions against this new campaign and, if possible, update their email policies to block “.one” attachments, at least from external email.